VMworld 2015 has come and gone, at least the US version. There were several sessions giving love to vCenter. This included the vCenter Server Appliance (VCSA). Here are a few of the sessions that are worth a look.
VMworld 2015 has come and gone, at least the US version. There were several sessions giving love to vCenter. This included the vCenter Server Appliance (VCSA). Here are a few of the sessions that are worth a look.
INF5975 – vCenter Server Appliance as First Choice VC
INF4528- vCenter Server Appliance VCSA Best Practices & Tips Tricks
INF4944- Managing vSphere 6.0 Deployments and Upgrades, Part 1
INF4945 – vCenter Server 6 High Availability
GUI Deployment
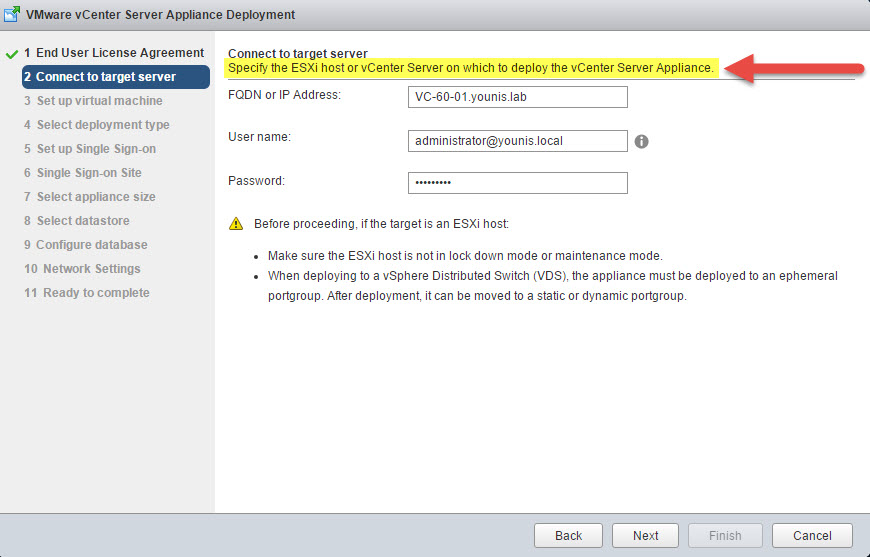
For a new deployment, you now have the option of two deployment targets. ESXi has been the only option until now, introducing vCenter Server as a deploy target.
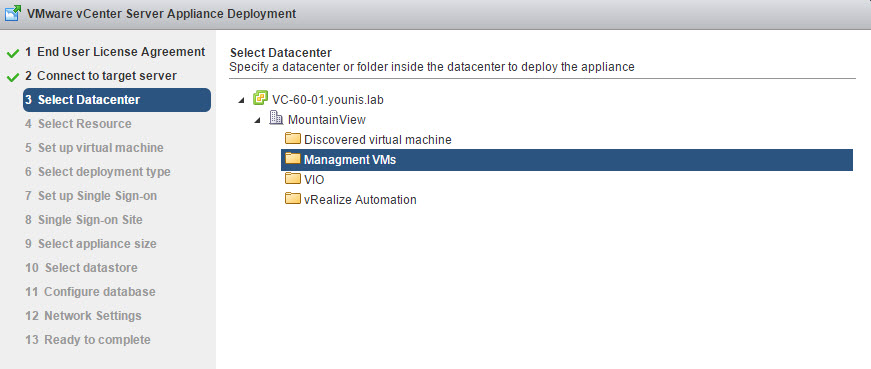
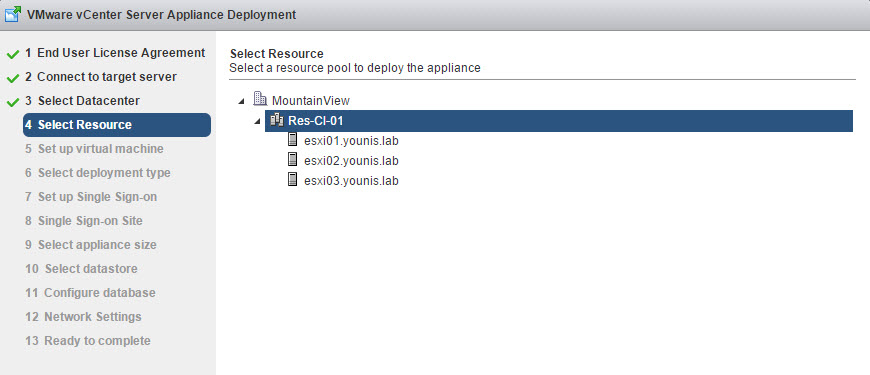
If you select vCenter Server as a target, two new options are added to the deployment menu on the left. The first is “Select Datacenter” and second, “Select Resource”. The rest of the deployment process is the same as before.
Scripted Deployment
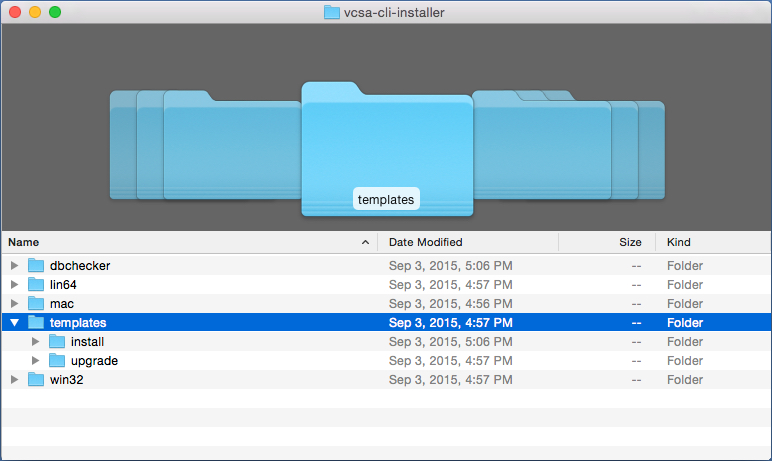
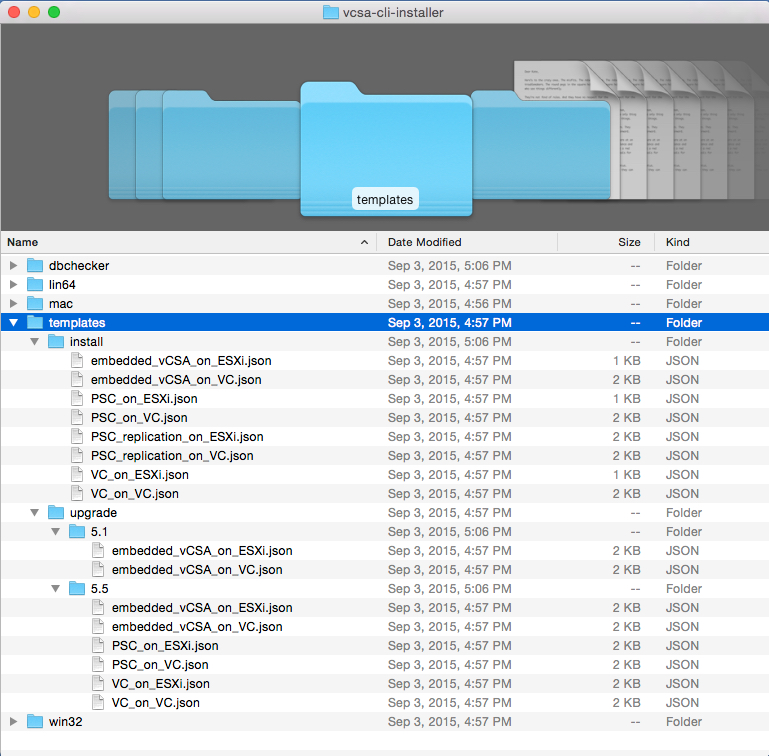
Aside from the GUI deployment, there is also a scripted deployment. This was also introduced in 6.0, but now with more additions. The VCSA-Cli-Installer directory\Templates directory contains the JSON scripts.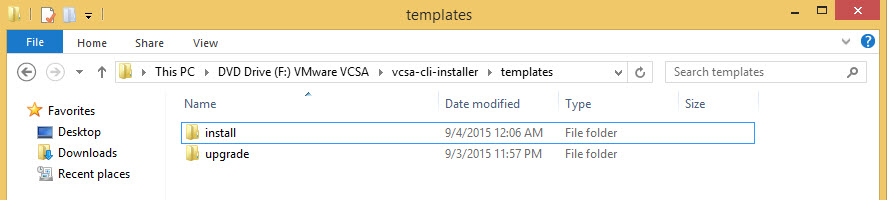
For new deployments utilize the scripts from the install directory. This directory now has 8 JSON scripts that spans both ESXi and vCenter.
Introduced in U1, an upgrade script method has been added. The upgrade directory has JSON scripts that allow upgrades from 5.1 U3 and 5.5. More on how to upgrade later.
More details about scripted VCSA deployments can be found here .
Upgrade
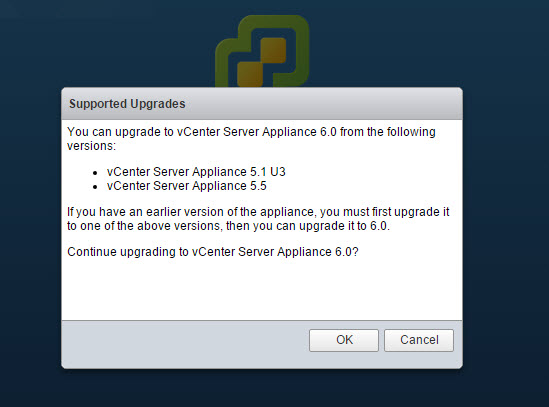
Note: Supported upgrade paths to VCSA 6.0 U1 include from 5.1 U3 & 5.5.
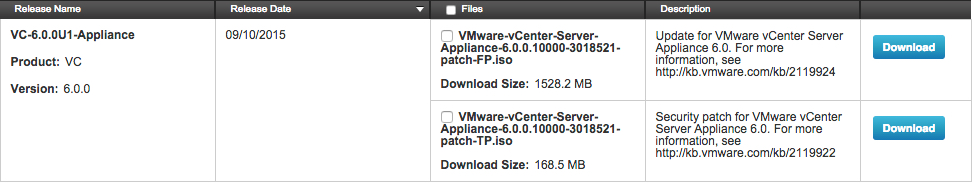
While on the topic of upgrades, going from VCSA 6.o to 6.0 U1 is quite simple. First, you’ll need a patch ISO, which can be found on here. You ‘ll notice there are two patch ISOs, FP and TP.
FP is a full product patch for VC & PSC appliances only.
TP is third party patch spanning multiple products, such as VCSA, vCenter Windows, VUM, PSC appliance and windows.
Note: Make sure you read the corresponding patch KB prior to upgrading.
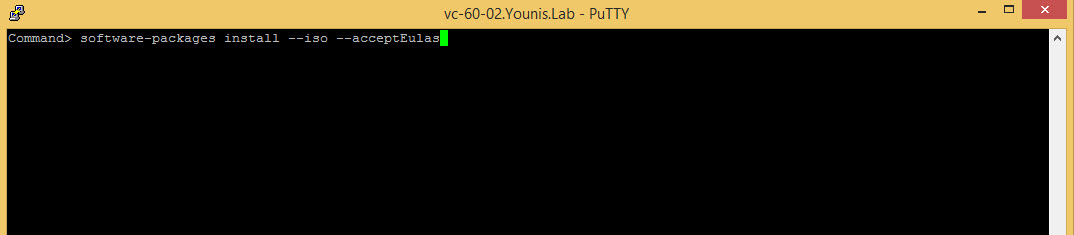
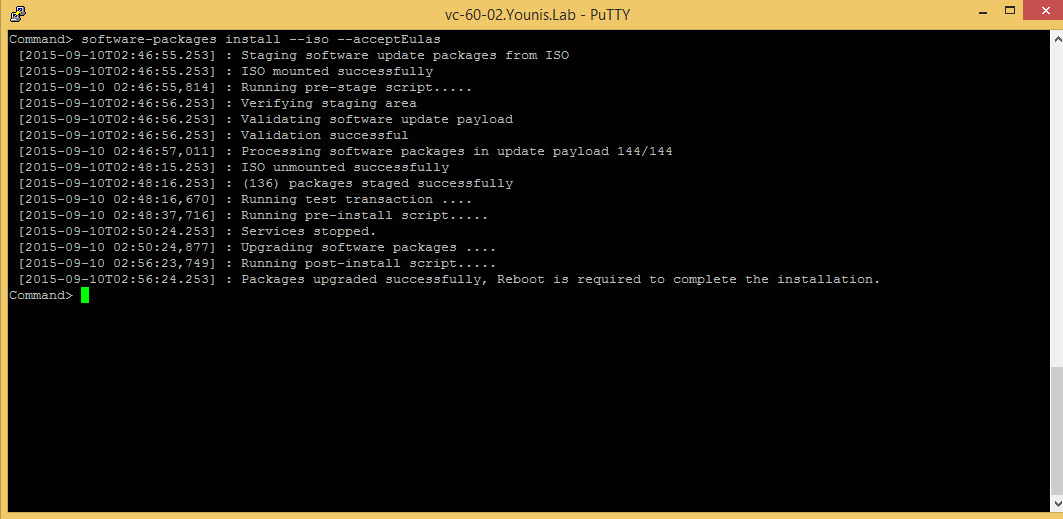
Attach the patch ISO to the VCSA cd-rom and run the following command “software-packages –install –iso –acceptEulas“.
After the upgrade is complete a reboot is required for the VCSA.
VCSA 5.1 U3 or 5.5 upgrades can be done from the 6.0 U1 ISO. Select Upgrade from the vcsa-setup and go through the wizard. You will need a temporary IP address, as the process deploys a new VCSA and ports over all the info. Once completed the old version of the VCSA will be shutdown.
As mentioned above scripted upgrades are also supported.
Virtual Appliance Management Interface (VAMI)
VCSA 6.0 was minus an old friend, the VAMI. VCSA 6.0 U1 the VAMI has returned! (applause). Not only is it back, but a with a new look in HTML5. To access the VAMI go to https://FQDN or IP of VCSA:5480.
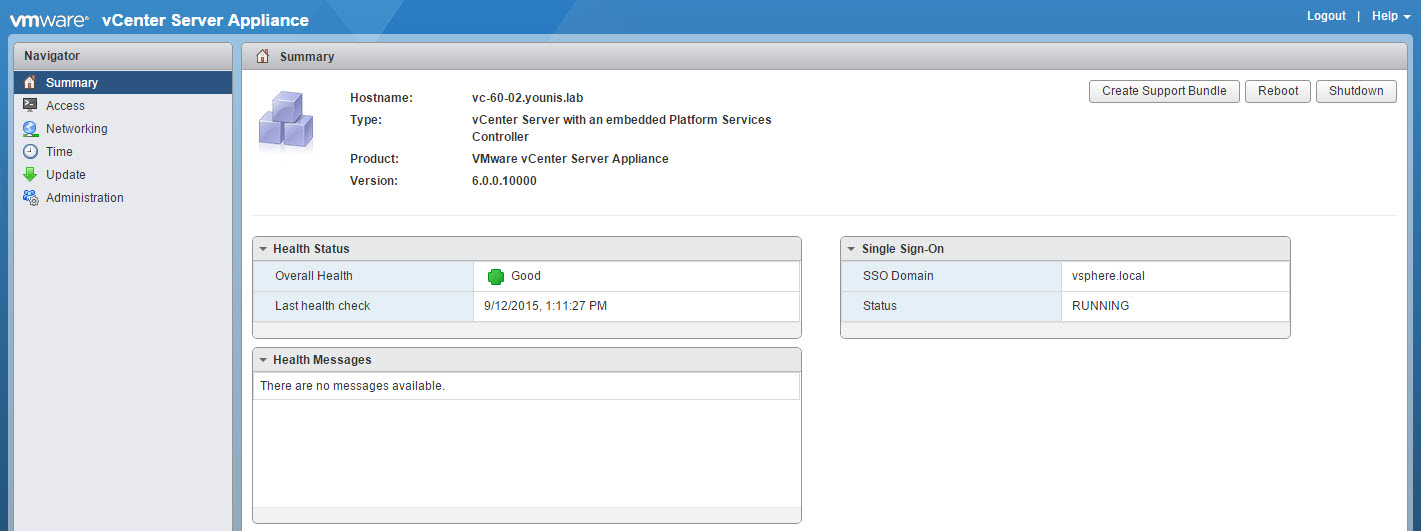
The new interface is definitely noticeable. Also the menus are now located on the left hand side of the UI instead of along of the top as in previous releases.
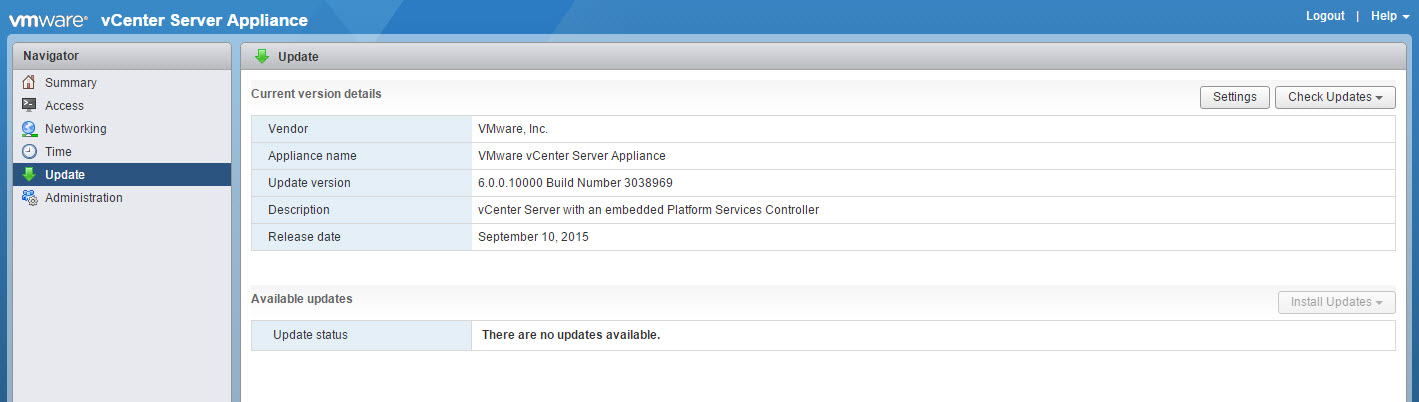
Two things that I would like to point out. First, the update menu has the ability to check for updates. This can be done atomically or by using a repository. Future updates will have the ability to be applied from here.
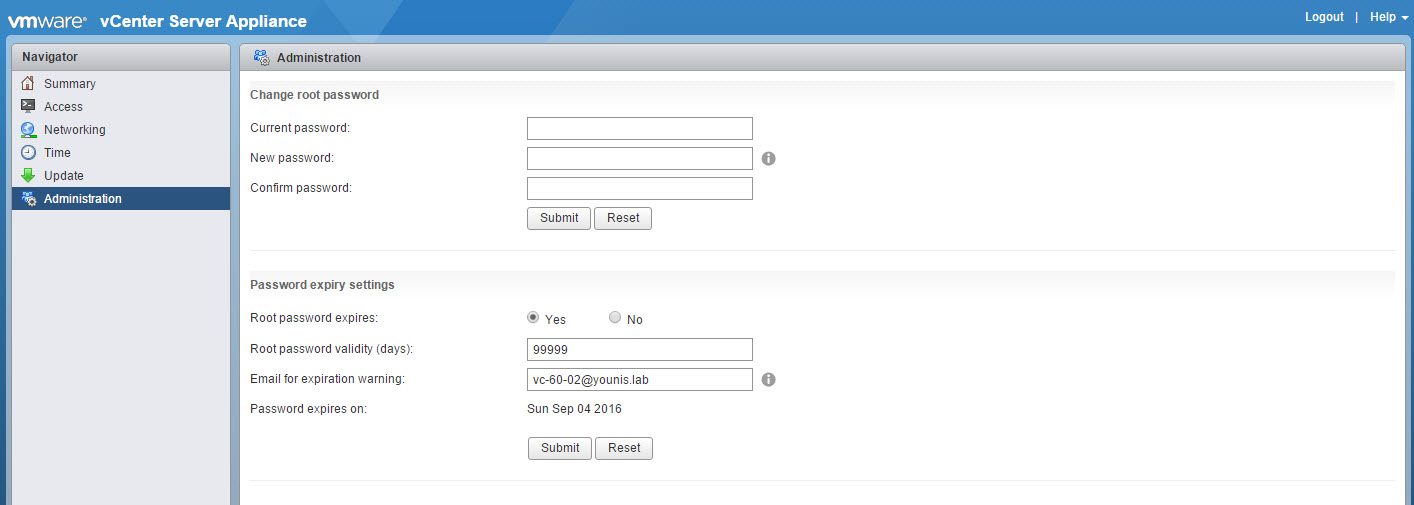
Secondly, the option to change your root password and expiration settings are under the administration menu. Make sure your vCenter SMTP is configured to received the expiration warnings. In case you were wondering the max number of days allowed is 99,999 (security!).
Web Client
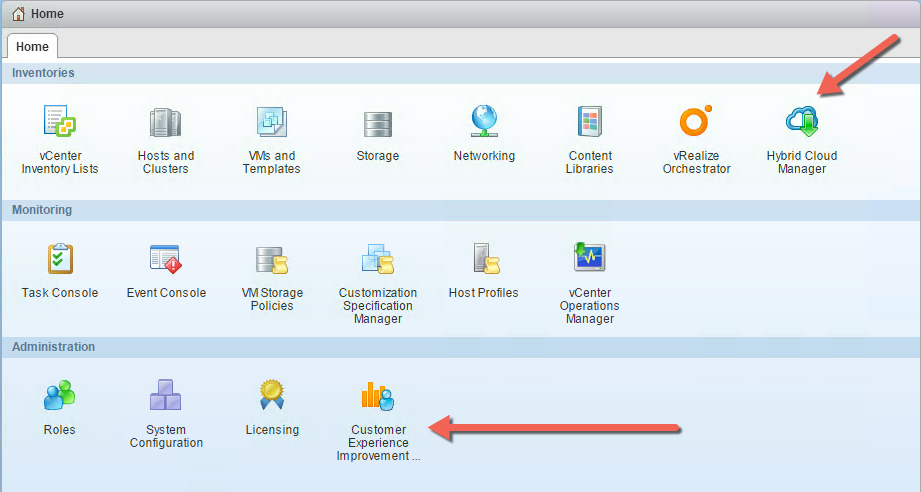
From the web client perceptive, two new icons have been added by default. The Hybrid Cloud Manager, which extends connectivity to vCloud Air. The other is the Customer Experience Improvement. There are no annoying messages asking to join and is disabled by default.
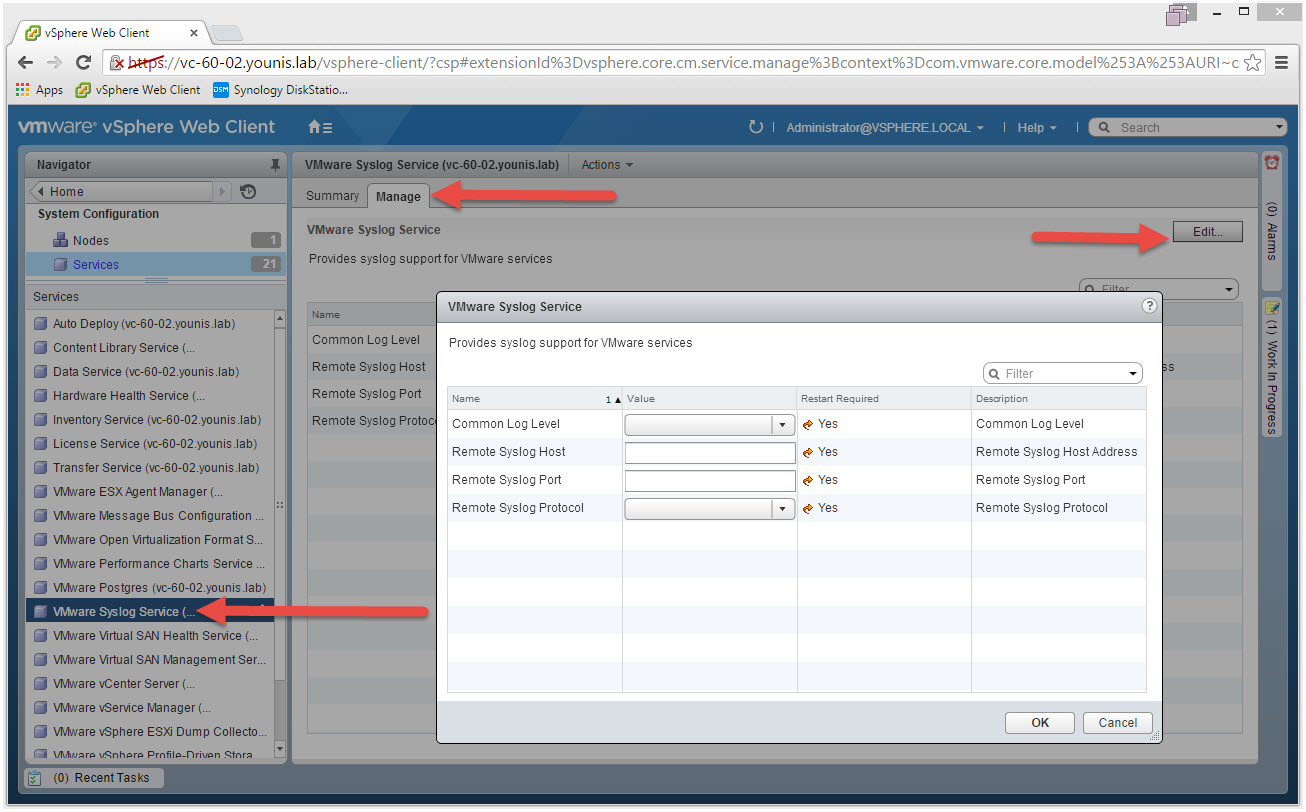
There is now an option to change to a remote syslog server. Go to System Configuration and select Services. Look for VMware Syslog Service and click the Manage tab.
VUM Integration
We finally have VMware Update Manager (VUM) integration in the web client, well sort of. A windows installation is still required for VUM. The upside is now all the VUM functions are now available in the web client, so we’re getting closer. Once VUM is pointed to vCenter, logout of the web client and back in, ta-da!
Note: This integration is also available with Windows version of vCenter
Backup / Restores
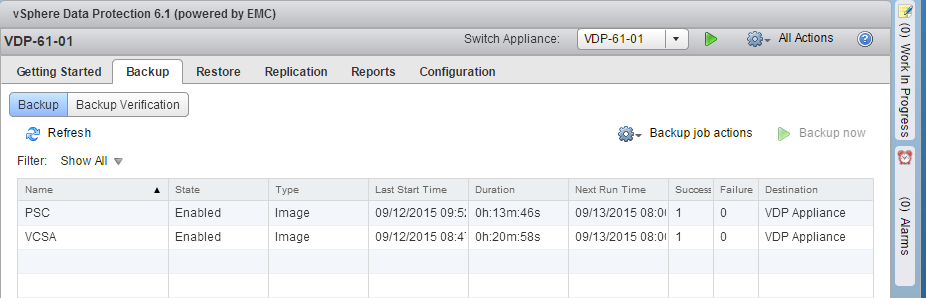
Support for VCSA backups via VMware vSphere Storage APIs – Data Protection (formley VADP) has been extended. In addition to VCSA with embedded PSC support, now external PSC has been added. This can be done leveraging VMware’s VDP or any third party solution with VMware vSphere Storage APIs – Data Protection, like Veeam. In this example I’m using VDP 6.1 and have taken backups of my external PSC and VCSA.
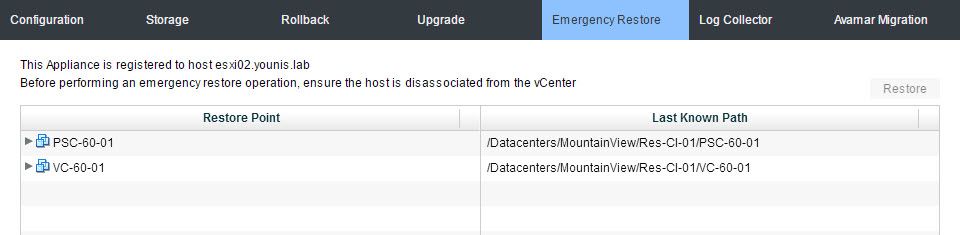
If corruption or a crash occurs to the VCSA and a restore is required are you prepared? Your solution although runs on VMware and is integrated with the VCSA should have a way to bring it back. In this example using VDP 6.1 Emergency Restore feature. Verify you have a solution or plan in place to bring the VCSA to life during such catastrophes.
Platform Services Controller (PSC)
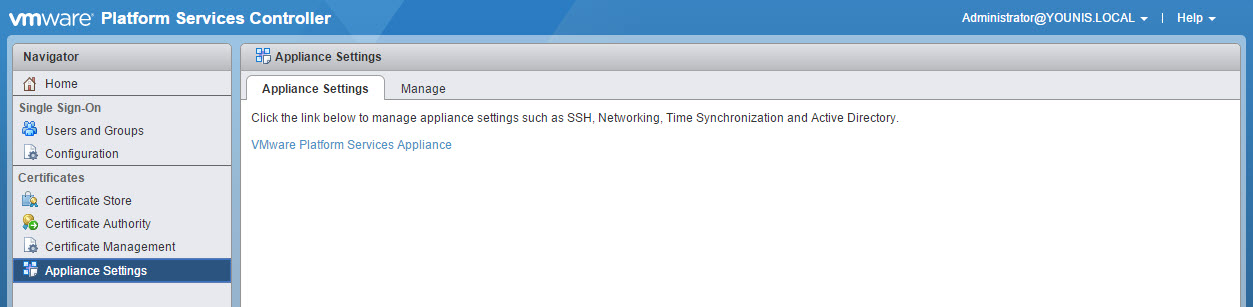
There are a couple new items for the Platform Services Controller with this release. PSC has a new UI just like the VAMI, in HTML5. To access go to https:// FQDN or IP of VCSA/PSC. This new UI is useful for troubleshooting and Certificate management. The appliance settings menu has a link to redirect to the VAMI, integration at its finest.
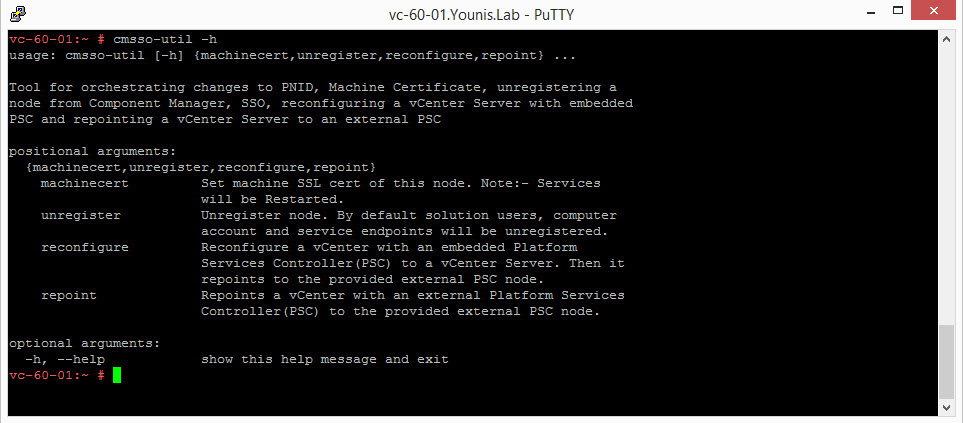
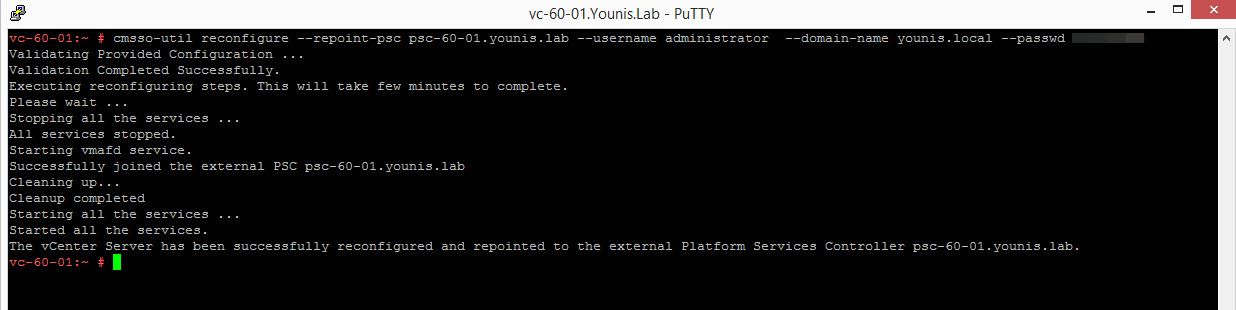
The command CMSSO-UTIL, now provides more flexibility. Allows you to repoint a VCSA with embedded PSC to external. This is great IMO so you no longer have to redeploy a new setup if you need to switch to an external PSC. Just make sure your PSC are in SSO domain.
As you can see, VCSA 6.0 update 1 is packed with a lot of goodness. VMware is definitely listening when it comes to vCenter, especially on the VCSA. This was more evident in this year’s sessions, with more detailed tech previews. I’m definitely looking forward to what the future holds for the VCSA.